What is Cybersecurity Mesh Architecture and Why Should You Care?
What exactly is CSMA, and why should you care? In this blog post, we'll delve into the intricacies of this emerging concept, exploring its definition, potential benefits, the process of creating a cybersecurity mesh, and which leading companies are already embracing its principles.
SECURITY
Richard Dean
6/6/20234 min read
In the ever-evolving realm of cybersecurity, staying ahead of the curve is not just a strategy; it's a necessity. The buzzword making waves in the cybersecurity community is "Cybersecurity Mesh Architecture" (CSMA). Coined by Gartner in 2022, it's more than just a marketing term; it's a visionary security architecture approach that promises to revolutionize the way organizations manage their security policies, tools, signals, and data.
But what exactly is CSMA, and why should you care? In this blog post, we'll delve into the intricacies of this emerging concept, exploring its definition, potential benefits, the process of creating a cybersecurity mesh, and which leading companies are already embracing its principles.
Decoding Cybersecurity Mesh Architecture
What is cybersecurity mesh architecture?
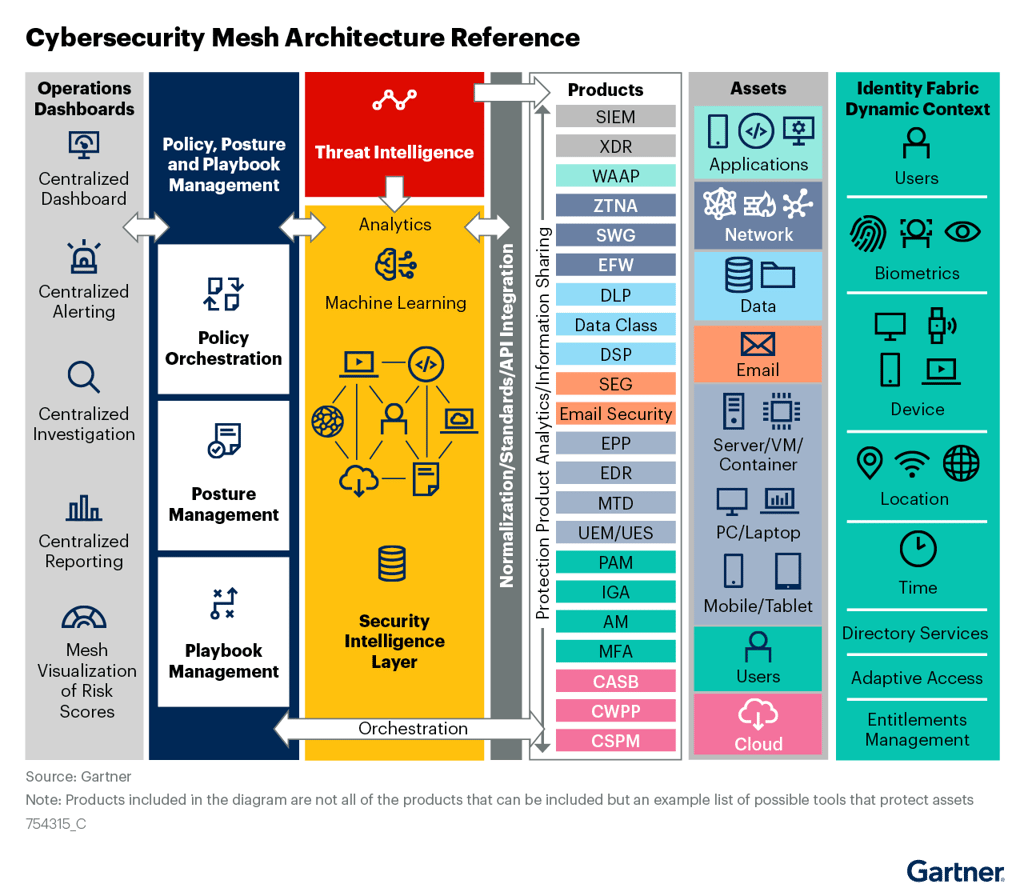
Cybersecurity mesh is a both a marketing term and a security architecture approach coined by Gartner in 2022 that calls for the flexible and scalable management of security policies, tools, signals, and data across an organization’s networks, endpoints, and identity fabric. It enables a “centralized decentralized” model, where security controls can be applied to any device, app, or identity, regardless of their location or platform.
Cybersecurity Mesh Benefits Unveiled
What are the benefits of cybersecurity mesh architecture?
I am not sure we know the benefits fully yet since this is a new visionary or aspirational framework, but the stated goals go something like this:
Reducing the complexity of information and processes is the primary goal.
A secondary goal is to find synergy across vendors but with fewer tools in the mix.
The final goal is to centralize signals, dashboards and processing while opening to new automation technologies such as AINetOps and AISecOps.
So, to sum it up, it’s calling for centralization of signals, visuals and management, simplification of understanding, integration across platforms and tools with an “artificial intelligence” layer that can interpret and collate all the different signals and ultimately lead to automation when required.
Blueprint for Cybersecurity Mesh Creation
How do you create a cybersecurity mesh architecture?
That is a harder and longer answer since it is not a tool or platform currently. First, I would say you need to take stock of your current tools and skills, then find your gaps and formulate a plan to augment those tools and skill gaps to work towards building a custom dashboard that is fed from the various tools you choose to use. Along with monitoring and evaluating the performance and effectiveness of your security mesh, you also need to adjust as needed.
Creating a cybersecurity mesh is not a one-time project, but an ongoing process that requires continuous assessment, planning, implementation, and improvement.
Industry Leaders Embracing Cybersecurity Mesh
What companies are using cybersecurity mesh architecture?
Honestly, everyone and no one. These are pretty core principles that most IT professionals attempt to follow normally. They are always trying to break down silos, centralize and build operations dashboards, and choose tools that integrate easily.
So, you ask, what companies are following this as part of their strategy? Well, I think most CISOs are aware of the concept and incorporate these frameworks into their overall strategies. At least I hope they do. But in terms of some large tech companies that have adopted or experimented with this approach, they include:
Google: Google uses a zero-trust network model called BeyondCorp, which applies granular security policies to every request based on the context and identity of the user, device, app, and data.
Microsoft: Microsoft has developed a cloud-based security platform called Azure Sentinel, which collects and analyzes data from various sources to provide a unified view and response to security incidents.
IBM: IBM offers a suite of security products and services that leverage AI and automation to enable a more integrated and intelligent security management system.
While each of these vendors does not fit the total bill when it comes to cybersecurity mesh architecture, these three big vendors do tackle some aspects of these concepts and may be the best way to move this approach forward through their eco-systems.
Strategic Shift: Positioning Your Organization for a Future of Rapid Change with CSMA
In the ever-evolving landscape of cybersecurity, Cybersecurity Mesh Architecture (CSMA) stands out as a promising and innovative approach, ushering in a paradigm shift from traditional security frameworks. The potential benefits it introduces make CSMA a compelling consideration for organizations aiming to fortify their security posture.
Yet, like any transformative concept, the success of CSMA relies on widespread adoption and collaboration. Similar to a presidential executive order requiring congressional support, CSMA depends on the cooperation of software vendors crafting individual security products. Without their buy-in, the crucial aspect of integration within CSMA may face challenges, particularly beyond the realm of large platform vendors.
"Position your organization for a future of rapid change by making a strategic shift in the way you buy and deploy security tools to align with CSMA. Even if a tool functions well today, if it doesn’t follow CSMA, it will not be flexible enough to meet future needs." – Gartner (G00754315)
Beyond vendor cooperation, the realization of CSMA's vision requires the development of an "artificial intelligence" layer. This layer plays a pivotal role in interpreting and collating diverse signals, paving the way for the automation of defense mechanisms. Without this crucial component, the laudable goal of integration alone falls short of addressing the multifaceted challenges faced by modern defenders, including alert exhaustion, insufficient visibility, and the complexities of correlation and centralization.
In conclusion, the success of CSMA hinges not only on technological advancements but also on fostering cooperation within organizations. This collaboration is crucial among diverse departments, including Identity Access Management (IAM), operations, network, and endpoint management, along with various security apparatuses.
CSMA underscores a significant challenge: the existing silos within organizations. In the technological realm, signals from network devices, endpoints, and identity are managed by separate teams. The same fragmentation is reflected in the teams overseeing these systems and signals. Until there is harmonized alignment in terms of resources and collaborative efforts across these departments, the adoption of such a transformative mandate may encounter obstacles.
The true potential of CSMA can only be realized when organizations break down internal barriers, facilitating seamless collaboration among departments. This cooperative spirit, extending beyond technological integration to encompass human collaboration, is paramount for the comprehensive success of Cybersecurity Mesh Architecture in addressing the evolving challenges of the digital landscape.
In essence, as organizations navigate the evolving threat landscape, a strategic shift aligned with CSMA becomes imperative. The wisdom embedded in Gartner's words underscores the importance of preparing for a future of rapid change. By embracing CSMA and fostering collaboration, organizations can position themselves not only to meet current challenges but also to navigate the dynamic and evolving cybersecurity landscape of tomorrow.


