Navigating the response phase of Identity Threat Detection and Response (ITDR)
ITDR is essential for protecting identity infrastructure. Learn what's most important in the response phase of ITDR.
SECURITY
Rich Dean
8/19/202410 min read
In our modern cybersecurity landscape, Identity Threat Detection and Response (ITDR) is essential for protecting identity infrastructure from sophisticated attacks. While preventive measures are crucial as discussed here, the response phase is vital for mitigating the impact.
This article outlines the key steps involved in the response phase of ITDR, helping organizations effectively manage and neutralize identity threats. Additionally, it covers core strategies in response playbooks, preventing human error, Active Directory (AD) recovery, and the role of Emergency Operations Centers (EOCs).
Key takeaways:
Response phase steps: Understanding and defining each step within the Containment, Eradication, Recovery, Reporting, and Remediation phases are crucial for effective response planning and execution.
Importance of a plan: Predefined playbooks and regular practice are essential; many organizations lack these.
Developing playbooks: Create detailed playbooks, conduct regular drills, and continuously update procedures.
Response strategies: Combine user training with advanced security technologies like anti-phishing, threat detection tools, and zero-trust models.
Active Directory recovery: Most organizations rely on Active Directory Domain Services (AD DS) but lack a proper plan and solution to recover from a ransomware attack. Use a phased approach and dedicated solutions for quick recovery of your Windows network.
Emergency Operations Center: Plan for EOCs for coordinated incident response during disaster recovery scenarios and ensure leadership roles are clearly defined for effective communication.
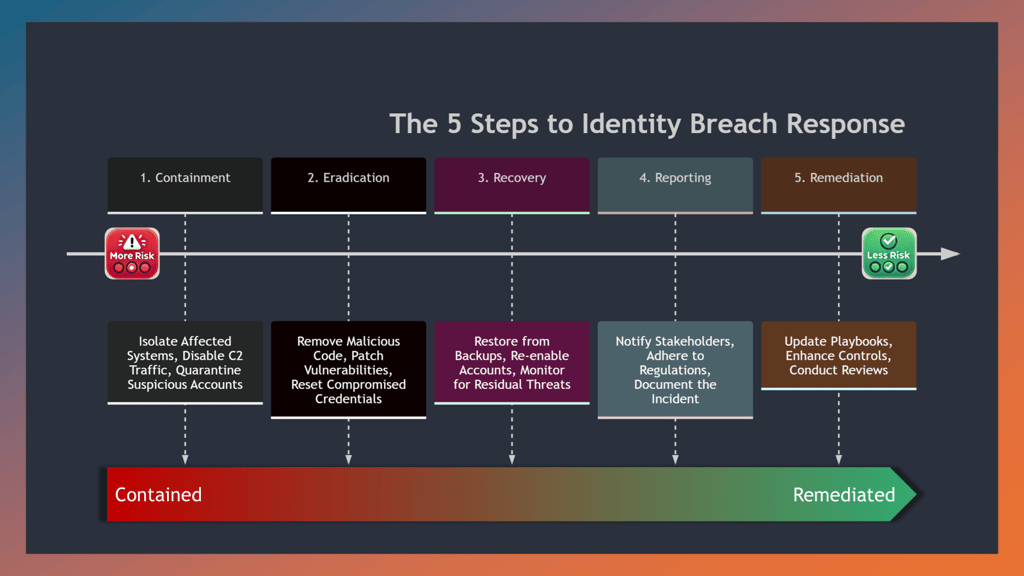
Key steps of the response phase
The response phase is a critical component of cybersecurity incident management. The phases of response for a cybersecurity incident are well-documented and established across different standards although they may be labeled, grouped or ordered differently. These standards outline a structured approach to managing the aftermath of a security breach or cyberattack, also known as a cybersecurity incident.
The process of responding to a cybersecurity incident can be broken down into five key steps: Containment, Eradication, Recovery, Reporting, and Remediation. Each step is crucial in ensuring an effective and efficient response to security incidents and being better prepared for future ones.
Containment
Isolate affected systems: Disconnect compromised systems from the network to prevent further spread.
Disable Command and Control Traffic (C2): Block attacker communication channels to cut off their control.
Quarantine suspicious accounts: Temporarily disable accounts that appear compromised.
Eradication
Remove malicious code: Use advanced scanning tools to detect and clean affected systems.
Patch vulnerabilities: Apply necessary patches to close security gaps.
Reset compromised credentials: Change passwords and potentially reset multifactor authentication (MFA) tokens for compromised accounts.
Recovery
Restore from backups: Use clean backups to restore systems to a known good state.
Re-enable accounts: Securely restore access to quarantined accounts after ensuring they are safe.
Monitor for residual threats: Continuously check for lingering threats and ensure they are eliminated.
Reporting
Notify stakeholders: Inform relevant parties, including management and affected users, about the incident.
Adhere to regulations: Ensure compliance with legal reporting requirements such as GDPR or CCPA.
Document the incident: Keep detailed records of the incident and the response actions taken.
Remediation
Update playbooks: Revise response procedures based on lessons learned from the incident.
Enhance controls: Strengthen Identity and Access Management (IAM) and ITDR measures.
Conduct reviews: Evaluate the response to improve future efforts.
By following these steps, organizations can ensure they are better prepared to handle cybersecurity incidents and minimize their potential impact. It’s important to note that these steps are not necessarily linear and may often occur concurrently or be revisited as new information about the incident comes to light. The key is to remain flexible and adaptable in the face of evolving cybersecurity threats.
The importance of having a plan
Gartner states as ITDR capabilities are new, there are few predefined identity-threat-specific playbooks to cover identity breaches and other types of attack on identity infrastructure (Gartner G00765882). The lack of predefined identity-threat-specific playbooks for breaches is a significant gap in many organizations’ preparedness, emphasizing the critical importance of having a predefined plan for responding to such incidents. Effective planning involves creating detailed playbooks, conducting regular drills, and continuously updating response procedures to reflect new threats and best practices.
At present, two major issues impede the effectiveness of response plans: the lack of identity-based playbooks and insufficient regular practice. Furthermore, the absence of industry-specific incentives to mandate emergency planning and practice can lead to organizations not prioritizing their ITDR strategies.
For instance, buildings have fire safety plans that include installing fire alarms, fire extinguishers, and emergency exit signs, and conducting regular fire drills. These measures are mandated by safety regulations because the potential danger and damage caused by a fire is clear and immediate to everyone. However, such clarity is absent when it comes to cybersecurity threats. As a result, emergency planning and practice are often left to the discretion of the stakeholders responsible for these duties within an organization and if they are not properly informed or motivated these practices can be overlooked.
Nevertheless, by implementing a robust ITDR plan with well-practiced and prioritized playbooks, organizations can better prepare themselves to handle identity threats.
Developing effective playbooks
To address these gaps, organizations should:
Create detailed playbooks: Develop comprehensive response procedures for specific types of identity breaches. These playbooks should outline step-by-step actions to be taken during an incident.
Conduct regular drills: Practice scenarios to ensure the team is prepared for real incidents. Regular drills help identify weaknesses in the response plan and ensure that team members are familiar with their roles and responsibilities during an incident.
Continuously update procedures: Regularly revise playbooks to reflect new threats and best practices. The cybersecurity landscape is constantly evolving, and response plans must be updated to address the latest threats and vulnerabilities.
Examples of playbooks and resources
Organizations looking to develop or enhance their ITDR plans can find playbooks and resources from various industry sources, including:
CISA: Cybersecurity Incident and Vulnerability Response Playbooks
MITRE: 11 Strategies of a World-Class Cybersecurity Operations Center
MITRE: Cyber Exercise Playbook
Microsoft Sentinel: This platform uses playbooks to automate and orchestrate threat response, ensuring rapid and efficient action during incidents.
Microsoft Incident Response Playbooks: These include detailed steps for different types of attacks such as phishing, password spray, and malicious applications, offering a structured approach to handling security incidents.
Microsoft’s Anti-Ransomware Playbook: This playbook outlines processes for preparing, detecting, responding to, and recovering from ransomware attacks, highlighting the importance of engaging stakeholders from across the organization.
Response strategies
During a discussion on the Practical 365 podcast with Microsoft’s Alex Weinert, VP of Identity Security, he emphasized a key point: “Organizations must not shy away from adding friction for end users to enhance security”. This insight is particularly relevant given the findings of the Verizon 2024 Data Breach Investigations Report (DBIR), which indicates that over 68% of breaches are due to human error, (such as clicking on a phishing email) not technical vulnerabilities.
The Verizon DBIR 2024 report further reveals that phishing remains a significant threat, with the click rate on phishing emails remaining consistent over the past two years. Despite extensive training efforts, the average time it takes for a user to click on a phishing link is about 20 seconds, highlighting the limitations of training alone in mitigating phishing risks. This points to the necessity of implementing robust technological safeguards alongside user education.
Key strategies to defend against human error:
Enhance training and awareness campaigns: Conduct annual training sessions and continuous awareness campaigns for employees on security best practices, including phishing awareness. These programs should incorporate phishing simulations to validate user response rates. However, training must be complemented with technology that can mitigate the risk of human error.
Leverage technology: Advanced security technologies can significantly reduce the reliance on human vigilance alone. Implementing threat detection tools like Microsoft Defender for Identity and Sentinel can identify and respond to threats in real-time. Multi-factor authentication (MFA) across all accounts adds an essential layer of security. Additionally, adopting passkeys offers secure and passwordless authentication. Email security solutions such as Proofpoint, Mimecast, and Barracuda can filter out malicious emails before they reach end users. Implementing User Behavior Analytics (UBA) tools to monitor user behavior and detect anomalies that may indicate compromised accounts is also crucial. Security Information and Event Management (SIEM) systems like Splunk and Microsoft Sentinel help collect, analyze, and respond to security events across the network. Lastly, utilizing Endpoint Detection and Response (EDR) solutions such as Microsoft Defender to monitor and protect endpoints from advanced threats enhances overall security posture.
Implement Zero Trust: Adopting a zero-trust security model ensures that all users, both inside and outside the network, are continuously verified. This approach minimizes the risk posed by compromised credentials and ensures tighter security controls.
Utilize comprehensive tools: Platforms such as Microsoft Sentinel offer automated playbooks to streamline incident response, while Microsoft’s Incident Response Playbooks provide detailed steps for handling specific types of attacks like phishing and ransomware. These tools are essential for a rapid and coordinated response to security incidents.
Understanding the importance of Active Directory recovery
In my experience, organizations often underestimate the critical role that Active Directory (AD) plays within their infrastructure, as well as the threats it faces. This misunderstanding can lead to inadequate planning and funding for the proper protection of AD against unauthorized changes and, in the worst-case scenario, ransomware.
Organizations may feel secure because they have enterprise backup solutions that do not specialize in AD, or they believe that the existing native tools are sufficient for their business needs. However, this is a significant issue. Enterprise backup solutions and native tools do not allow for the granular restoration of objects and attributes that have been changed, nor do they allow for fast restoration during a total outage.
In addition, AD is considered a Tier Zero or critical asset, which makes it a prime target in attacks due to its role as the primary source of identity and access management in enterprises. Restoring AD is not as simple as restoring an operating system. Without the proper capabilities, restoring AD without existing compromises and in an automated fashion to recover as quickly as possible can be challenging.
Gartner’s report, “Implement IAM Best Practices for Your Active Directory (G00762644),” recommends accelerating recovery from attacks by adding a dedicated tool for the backup and recovery of Microsoft Active Directory. Despite this advice, many organizations lack confidence in their ability to quickly recover from a large-scale Active Directory attack.
The most efficient way to restore operations after a disaster is through a phased recovery approach. This method involves initially restoring key domain controllers to resume basic operations, followed by a more comprehensive restoration process. Automated Active Directory recovery solutions can dramatically reduce Active Directory downtime, accelerating the return to normal operations and minimizing the costs of the disaster.
Equally important and cannot be overstated is having a planned or predetermined prioritization of critical business processes during disaster recovery. This is not something that should be figured out amid a crisis. It is crucial that this information is communicated to all employees, extending beyond just the IT and Security departments.
Consider, for instance, which business functions, applications, geographies, or business units should receive immediate attention to restore business operations? The answer to this may not necessarily be related to the type of breach that has occurred. It usually requires the involvement of Line of Business (LOB) executives and strategists during the recovery design phase.
A generic playbook will not provide this level of detail. These considerations must be discussed and incorporated during the customization of the playbook. This ensures that the response to any potential disaster is tailored to the specific needs and priorities of the business.
In the context of Active Directory recovery, expanding ITDR as a practice involves training security operations staff in Identity and Access Management (IAM) and breaking down the barriers that exist between them. Otherwise, the proper solutions will not be identified to properly protect AD and other IAM systems. Organizations should seriously look at their AD recovery plans and how long it will take to recover from a scorched earth scenario. If they don’t know, they need to find out.
Running an Emergency Operation Center
When most people envision an emergency operation center, they typically do not think about cybersecurity incidents. However, in today’s digital age, cybersecurity threats are as real and potentially damaging as any physical disaster.
Take for example a significant incident in 2024, when a ransomware attack against Change Healthcare, a prescription processor owned by UnitedHealth, caused massive disruption in the U.S. healthcare system for weeks. The attack prevented many pharmacies and hospitals from processing claims and receiving payments, disrupting critical care and potentially leading to a loss of life. This is not the first known case where a cyberattack had life-or-death consequences, nor will it be the last.
This real-world example underscores the importance of having robust cybersecurity measures in place, including a well-prepared emergency operation center. It’s a stark reminder that in our interconnected world, cybersecurity is not just about protecting data – it’s about protecting lives.
To get some more insights on this topic I reached out to Andy Jaw. Andy is a retired United States Air Force Captain and law enforcement professional who is now a cybersecurity specialist at Microsoft. Andy shared his unique insights from his years of varied experiences in different roles during emergency situations. During our conversation on the Practical 365 podcast Andy emphasized the importance of having an Emergency Operations Center (EOC) as part of a comprehensive cyberattack response playbook because natural disasters aren’t the only incidents that can cause mass disruption to an organization anymore. Andy highlighted four key considerations for EOCs:
Quick setup: Establish EOCs rapidly in response to incidents, defining the types of incidents that would necessitate an EOC. Identity-based incidents may not always warrant the need for an EOC, but it is important to include EOC activation as part of your disaster recovery playbooks.
Leadership: Appoint a designated leader with authority and expertise from each business function. Clearly delineate roles and responsibilities between EOC leadership, incident commanders in the field, and executive decision-makers. This ensures a coordinated and effective response to incidents.
Command and control: Establish a command center in a safe location from incidents, such as inclement weather. This command center should be equipped with the necessary resources to manage the incident effectively.
Coordination and communications: Ensure effective and redundant communication and coordination among all stakeholders, utilizing primary and secondary methods of communication. This ensures that everyone involved is informed and can respond appropriately to the incident even when primary communication lines are down too.
This incident and many others serve as powerful examples of how an EOC can be effectively used to manage a cybersecurity crisis like a ransomware attack that ultimately, protects lives. It also underscores the importance of having robust cybersecurity measures in place, including a well-prepared EOC.
Strengthening your ITDR strategy
Effectively managing and mitigating identity threats requires a comprehensive approach that encompasses all phases of the response. By understanding and implementing the key steps in the response phase, developing detailed playbooks, leveraging advanced security technologies, and ensuring robust recovery plans, organizations can significantly enhance their ITDR capabilities. Additionally, the establishment of Emergency Operations Centers (EOCs) and continuous training and drills ensure a well-prepared response to any identity-based incidents. These strategies collectively fortify an organization’s defenses, ensuring resilience against increasingly sophisticated cyber threats.
Sources:
Implement IAM Best Practices for Your Active Directory (gartner.com)
How to Protect Backup Systems From Ransomware Attacks (gartner.com)
Data Breach Investigations Report 2024. Verizon
Ransomware attack on U.S. health care payment processor ‘most serious incident of its kind’ (NBC News)
8 critical lessons from the Change Healthcare ransomware catastrophe (CSO Online)
Active Directory disaster recovery: Creating an airtight strategy. Quest
Practical 365 Podcast, Episode S4 E20, “Mastering ITDR Response – Insights from Microsoft’s Andy Jaw” Practical 365
CISA: Cybersecurity Incident and Vulnerability Response Playbooks
MITRE: 11 Strategies of a World-Class Cybersecurity Operations Center
MITRE: Cyber Exercise Playbook


